Kaspersky uncovers phishing using SendGrid to target SMBs, exploiting stolen credentials for authentic-looking emails, easily deceiving recipients.
Cybercriminals often target mailing lists companies use to reach their customers, presenting opportunities for spamming, phishing, and other sophisticated scams. Access to legitimate tools for sending bulk emails further enhances the success rates of such attacks. Consequently, attackers frequently attempt to compromise companies’ accounts with email service providers (ESPs). In its latest research, Kaspersky discovered a phishing campaign that refined this attack method by harvesting the credentials of the SendGrid ESP and sending phishing emails directly through the ESP itself.
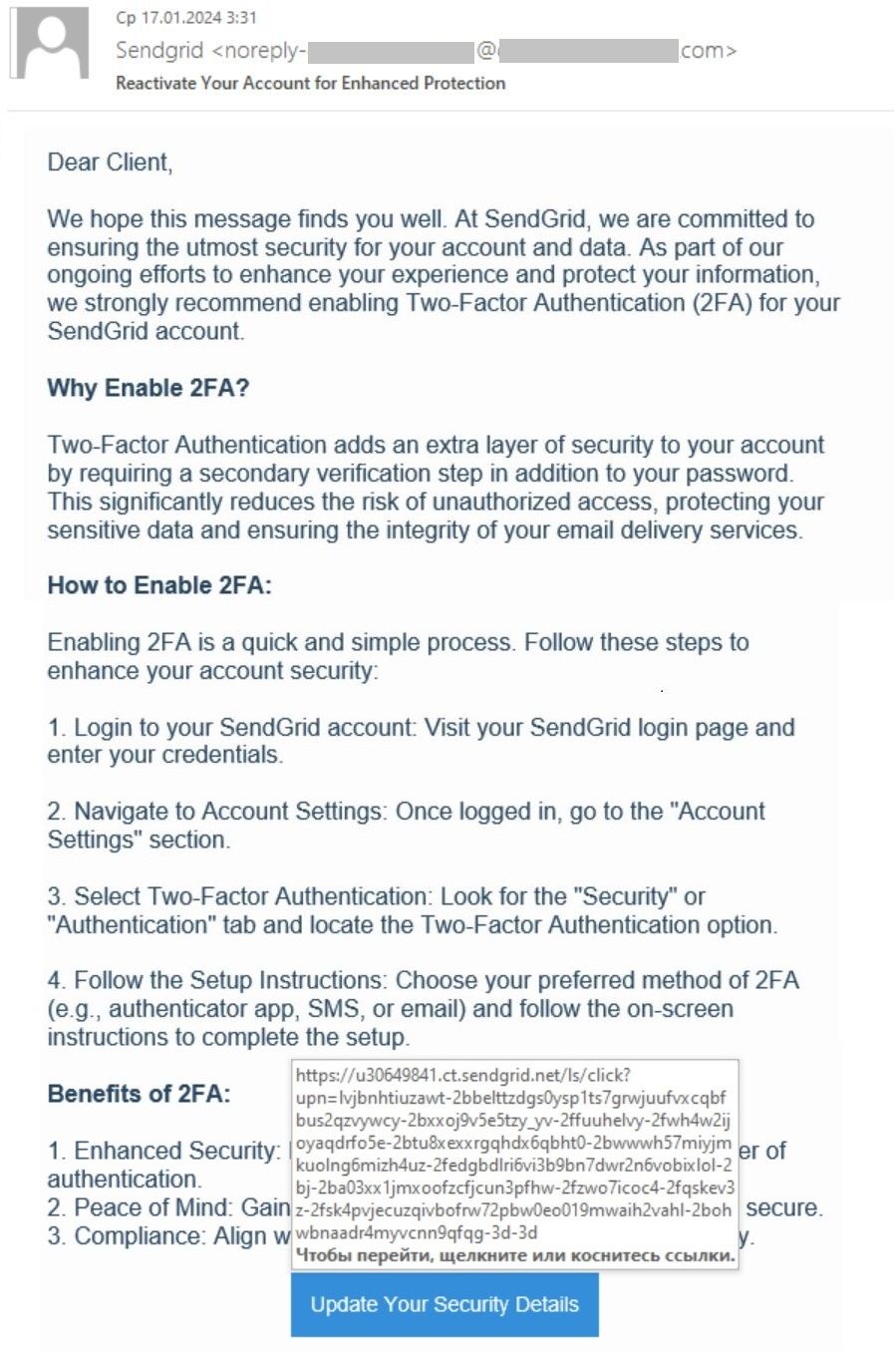
By sending phishing emails directly through the ESP, attackers increase the likelihood of success, capitalizing on recipients’ trust in communications from familiar sources. The phishing emails originate from SendGrid, expressing concern about security and urging recipients to enable two-factor authentication (2FA) to protect their accounts. However, the provided link redirects users to a fraudulent website mimicking the SendGrid login page, where their credentials are harvested.
To all email scanners, the phishing looks like a legitimate email sent from SendGrid’s servers with valid links pointing to the SendGrid domain. The only thing that may alert the recipient is the sender’s address. ESPs put the real customer’s domain and mailing ID there. An important sign of fraud is the phishing site’s “sendgreds” domain, which closely resembles the legitimate “sendgrid” at first glance, serving as a subtle yet significant warning sign.
This campaign is particularly insidious because the phishing emails bypass traditional security measures. Since they are sent through a legitimate service and contain no obvious signs of phishing, they may evade detection by automatic filters.
“Using a reliable email service provider is important for your business’ reputation and safety. However, some sneaky scammers learned how to mimic reliable services – so it is crucial to check the emails you receive properly, and, for better protection, install a reliable cybersecurity solution,” comments Roman Dedenok, a security expert at Kaspersky.
Most often, phishers use hijacked accounts because ESPs subject new customers to rigorous checks, while old ones who have already fired off some bulk emails are considered reliable.
Read more about this phishing campaign on Kaspersky Daily.
To keep your data protected from phishing attacks and leaks, Kaspersky experts recommend:
- Provide your staff with basic cybersecurity hygiene training. Conduct a simulated phishing attack to ensure your employees know how to distinguish phishing emails.
- Use protection solutions for mail servers with anti-phishing capabilities to decrease the chance of infection through a phishing email. Kaspersky Security for Mail Server prevents your employees and business from being defrauded by socially engineered scams.
- Use a protection solution for endpoints and mail servers with anti-phishing capabilities, such as Kaspersky Endpoint Security for Business, to decrease the chance of infection through a phishing email.
- If using Microsoft 365 cloud service, don’t forget to protect it too. Kaspersky Security for Microsoft Office 365 has a dedicated anti-spam and anti-phishing protection for SharePoint, Teams and OneDrive apps for secure business communications.
- Use lightweight, easy-manageable, but effective solutions such as Kaspersky Small Office Security. It helps prevent being locked out of your computer due to phishing emails or malicious attachments.
- I am seeking a dedicated solution for small and medium businesses with simple management and proven protection features, such as Kaspersky Endpoint Security Cloud. File Threat Protection, Mail Threat Protection, Network Threat Protection, and Web Threat Protection within the product include technologies that shield users from malware, phishing, and other threats.



