Nearly 40% of industrial control systems were attacked in 2023, with building automation being the most targeted sector. Kaspersky reports details of threats and offers security recommendations for OT networks.
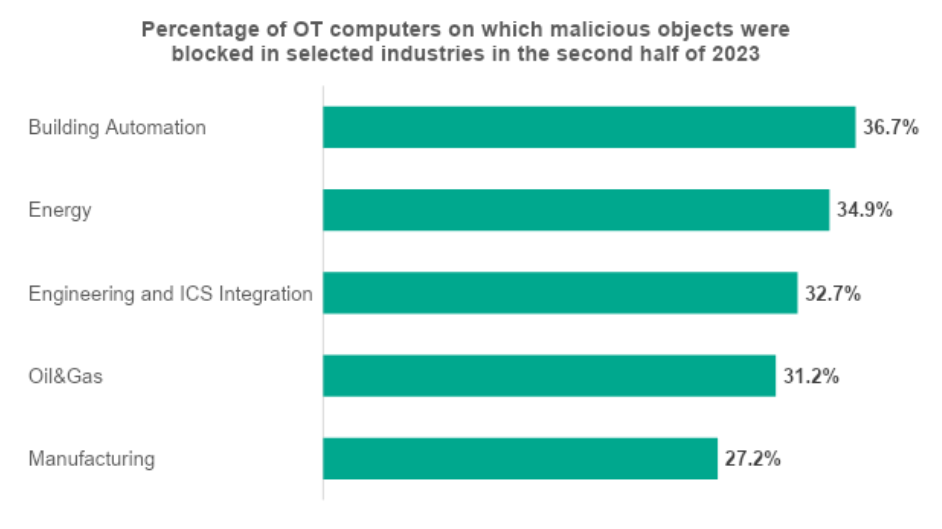
Kaspersky’s ICS CERT (Industrial Control Systems Cyber Emergency Response Team) unveils an Operational Technology (OT) cybersecurity trends analysis for the second half of 2023. With a yearly average of 38.6% of OT computers attacked in 2023, the report identifies Automation of buildings as the sector most exposed to threats (in the second half of 2023, malicious objects were blocked on 36.7% of OT computers in that industry), followed by Energy sector (34.9%), Engineering and ICS Integration (32.7%), Oil&Gas (31.2%), Manufacturing (27.2%).
The landscape of threats in the second half of 2023 remained diverse and multifaceted, with threats spreading via the internet as the main source of cyber risks to OT computers, accounting for 18.1% of the attacks, followed by email clients at 4% and removable media at 1.9%.
Kaspersky security solutions blocked malware that belonged to 12,618 families on industrial automation systems. Malicious objects belonged to several categories; among the most widespread were malicious scripts and, phishing pages, denylisted internet resources.
Also Read: Explained: Information Security Management System (ISMS)
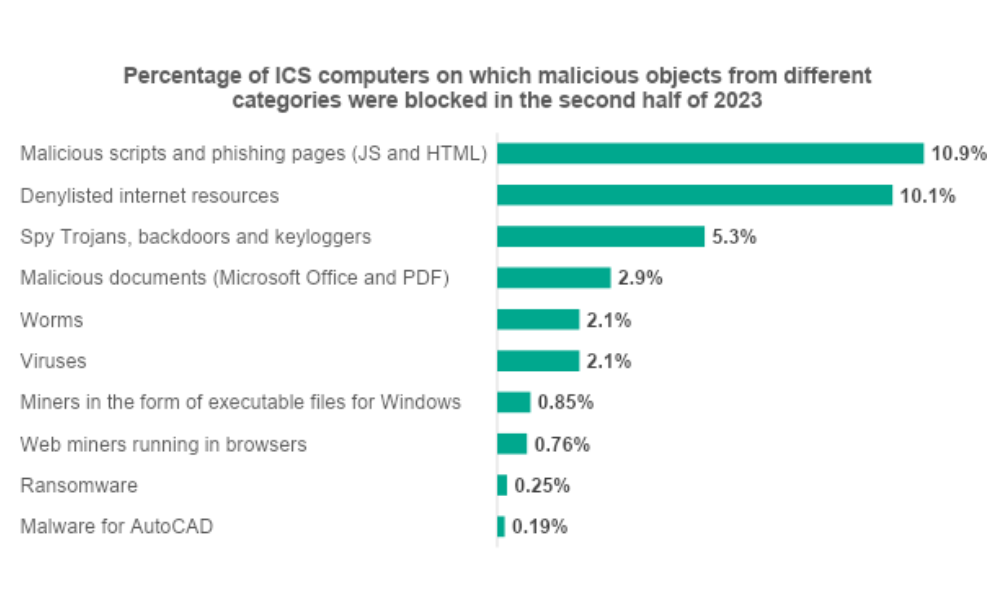
“Malicious objects that our solutions block can be grouped into three categories: those used for initial infection (such as dangerous web resources, malicious scripts, malicious documents), next-stage malware (including spyware, ransomware or miners) delivered to a victim in most cases via the internet or email, and self-propagating malware (worms and viruses). All of these can be extremely harmful to an organization. We investigated cases when even far-from-industrial malware, such as a banking trojan, nearly stopped factory operations,” comments Evgeny Goncharov, Head of Kaspersky’s ICS CERT. “With this in mind, industrial companies should continue fortifying their defenses by tailoring their cybersecurity strategies and staying informed about the ever-evolving threats.”
To keep OT computers protected from various threats, Kaspersky experts recommend the following:
- Conducting regular security assessments of OT systems to identify and eliminate possible cyber security issues.
- Establish continuous vulnerability assessment and triage as a foundation for an effective vulnerability management process. Dedicated solutions like Kaspersky Industrial CyberSecurity may become an efficient assistant and a source of unique, actionable information not fully available to the public.
- Performing timely updates for the key components of the enterprise’s OT network, applying security fixes and patches, or implementing compensating measures as soon as possible is crucial for preventing a major incident that might cost millions due to the interruption of the production process.
- Using EDR solutions such as Kaspersky Endpoint Detection and Response for timely detection of sophisticated threats, investigation, and effective remediation of incidents.
- Improving the response to new and advanced malicious techniques by building and strengthening teams’ incident prevention, detection, and response skills. Dedicated OT security training for IT security staff and OT personnel is one of the key measures helping to achieve this.



